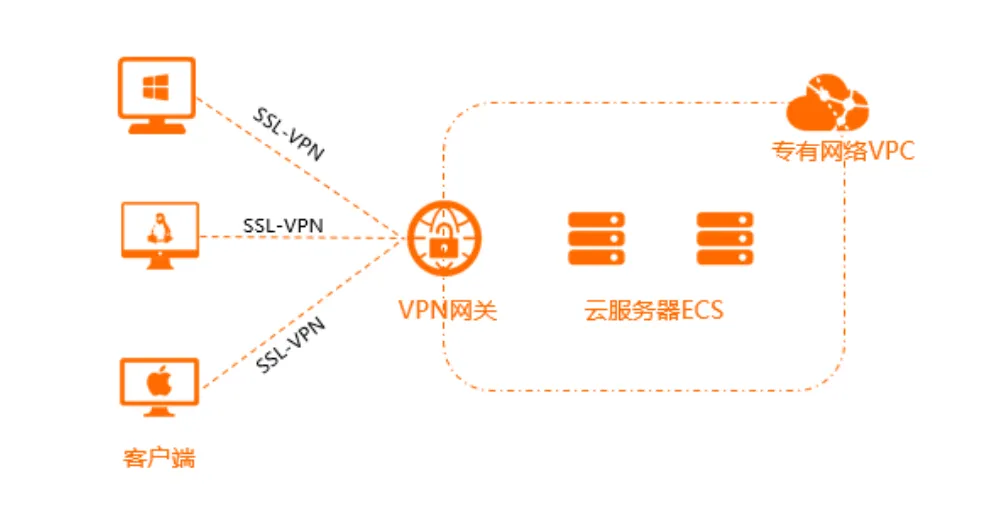
服务端安装
修改网络防火墙规则
默认VPN的端口无法访问,修改网络防火墙规则,添加1规则实现1194/TCP/UDP端口允许通过
相关程序安装
apt update
//查看安装版本
apt list openvpn
//安装openvpn以及证书颁发工具相关
apt install openvpn easy-rsa准备相关配置文件
cd /opt/ & mkdir easy-rsa & cd easy-rsa
#准备证书颁发相关文件
cd /usr/share/easy-rsa/ & mv ./* /opt/easy-rsa/
cd /opt/easy-rsa/
#准备颁发证书相关变量的配置文件
cp vars.example varsvim cars
#CA的证书默认有效期为10年,可以适当延长,比如:36500天
#set_var EASYRSA_CA_EXPIRE 3650
set_var EASYRSA_CA_EXPIRE 36500
#服务器证书默为为825天,可适当加长,比如:3650天
#set_var EASYRSA_CERT_EXPIRE 825
#将上面行修改为下面
set_var EASYRSA_CERT_EXPIRE 3650准备证书相关文件
#初始化PKI生成PKI相关目录和文件,可以用tree命令观察多了什么文件目录
./easyrsa init-pki
#创建 CA 机构证书环境
./easyrsa build-ca nopass#执行内容:Common Name (eg: your user, host, or server name) [Easy-RSA CA]: #回车接受默认值#创建服务器证书申请文件,其中server是文件前缀
./easyrsa gen-req server nopass#执行内容:Common Name (eg: your user, host, or server name) [server]: #接受Common Name的默认 值,直接回车#颁发服务端证书,第一个server表示证书的类型,第二个server表示请求文件名的前缀
./easyrsa sign server server#Confirm request details: yes #输入yes回车#创建密钥
./easyrsa gen-dh客户端证书申请以及颁发
#创建客户端证书申请
./easyrsa gen-req wangqing nopass
#颁发客户端证书
./easyrsa sign client wangqing服务器证书转移
#将CA和服务器证书相关文件复制到服务器相应的目录
cp pki/ca.crt /etc/openvpn/server/
cp pki/issued/server.crt /etc/openvpn/server/
cp pki/private/server.key /etc/openvpn/server/
cp pki/dh.pem /etc/openvpn/server/客户端证书转移
#将客户端私钥与证书相关文件复制到服务器相关的目录
mkdir /etc/openvpn/client/wangqing
cp /opt/easy-rsa/pki/ca.crt /etc/openvpn/client/wangqing/
cp /opt/easy-rsa/pki/private/wangqing.key /etc/openvpn/client/wangqing/
cp /opt/easy-rsa/pki/issued/wangqing.crt /etc/openvpn/client/wangqing/服务器配置文件
查看配置选项
cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf /etc/openvpn/
cd /etc/openvpn/
#服务器配置文件server.conf文件中以#或;开头的行都为注释
grep -Ev "^#|^$" /etc/openvpn/server.conf;local a.b.c.d #本机监听IP,默认为本机所有IP
port 1194 #端口
;proto tcp #协议,生产推荐使用TCP
proto udp #默认协议udp
;dev tap #创建以太网隧道设备,tap设备实现以太网帧通过Openvpn隧道,可提供非IP协议如
IPX和AppleTalk等的支持,tap等当于一个以太网设备,它操作第二层数据包如以太网数据帧。
dev tun #创建IP路由隧道,生产推存使用tun.互联网使用tun,一个tun设备大多时候被用于基
于IP协议的通讯。tun模拟了网络层设备,操作第三层数据包比如IP数据封包。
;dev-node MyTap #TAP-Win32的设备驱动。非windows系统不需要
ca ca.crt #ca证书文件
cert server.crt #服务器证书文件
key server.key #服务器私钥文件
dh dh2048.pem #dh参数文件
;topology subnet
server 10.8.0.0 255.255.255.0 #客户端连接后自动分配的IP网段,默认会给服务器分配此网段的
第一个IP将做为客户端的网关,注意不要和内网网段相同
ifconfig-pool-persist ipp.txt #记录客户端和虚拟ip地址分配的文件
;server-bridge 10.8.0.4 255.255.255.0 10.8.0.50 10.8.0.100 #配置网桥模式,无需配置,
建议注释
;server-bridge
;push "route 192.168.10.0 255.255.255.0" #推送给客户端的到达服务器后面网段的静态路由,
网关是服务器地址10.8.0.1
;push "route 192.168.10.100 255.255.255.255" #用255.255.255.255可实现只能访问内网单
个主机的功能,比如:jumpserver
;push "route 192.168.20.0 255.255.255.0" #推送路由信息到客户端,以允许客户端能够连接到
服务器背后的其它私有网络
;client-config-dir ccd #为特定客户端添加路由信息,此路由是客户端后面的网段而非服务端的网
段,无需设置
;route 192.168.40.128 255.255.255.248
;client-config-dir ccd
;route 10.9.0.0 255.255.255.252
;learn-address ./script #指定外部脚本文件,实现创建不同组的iptables规
则,无需配置
;push "redirect-gateway def1 bypass-dhcp" #启用此配置后客户端所有流量都将通过VPN服务器
进行转发,因此生产一般无需配置此项
;push "dhcp-option DNS 208.67.222.222" #推送DNS服务器地址,无需配置
;push "dhcp-option DNS 208.67.220.220"
;client-to-client #允许不同的客户端直接通信,不安全,生产环境一般无
需配置
;duplicate-cn #多个用户共用一个证书,一般用于测试环境,生产环境建议一个用户一个证
书,无需开启
keepalive 10 120 #设置服务端活动的检测的间隔和超时时间,每隔10秒ping一次,120秒没
有回应则认为已经断线
tls-auth ta.key 0 #访止DoS等攻击的安全增强配置,服务器和每个客户端都需要拥有此密钥文
件。第二个参数在服务器端为0,客户端为1
cipher AES-256-CBC #加密算法修改服务器端配置文件
vim /etc/openvpn/server.conf
``
port 1194
proto udp
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key # This file should be kept secret
dh /etc/openvpn/server/dh.pem
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /var/log/openvpn/ipp.txt
keepalive 10 120
cipher AES-256-CBC
max-clients 50
user root
group root
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 6
mute 20
explicit-exit-notify 1
``准备服务器日志相关目录
adduser --system --home /etc/openvpn --ingroup openvpn --shell /usr/sbin/nologin openvpn
chown -R openvpn:openvpn /etc/openvpn
mkdir /var/log/openvpn
chown openvpn.openvpn /var/log/openvpn启动 OpenVPN 服务
systemctl start openvpn@server验证服务
systemctl status openvpn@server
ss -ntlp | grep 1194验证网卡
ip a
``
46: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 500
link/none
inet 10.8.0.1/24 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::463f:5825:8bf4:5e2/64 scope link stable-privacy
valid_lft forever preferred_lft forever
``准备 OpenVPN 客户端配置文件
grep '^[[:alpha:]].*' /usr/share/doc/openvpn/examples/sample-config-files/client.conf > /etc/openvpn/client/wangqing/client.ovpn
vim /etc/openvpn/client/wangqing/client.ovpn
``
client
dev tun
proto udp
remote 8.140.50.20 1194
resolv-retry infinite
nobind
#persist-key
#persist-tun
ca ca.crt
cert wangqing.crt
key wangqing.key
remote-cert-tls server
#tls-auth ta.key 1
cipher AES-256-CBC
verb 3
``客户端配置文件简化
client
dev tun
proto udp
remote 8.140.50.20 1194
route 10.8.0.0 255.255.255.0
resolv-retry infinite
nobind
<ca>
-----BEGIN CERTIFICATE-----
MIIDSzCCAjOgAwIBAgIUJXoAKaUkCVOnWLTGS7/AT462TBUwDQYJKoZIhvcNAQEL
BQAwFjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjMxMDEzMDI1NzAzWhcNMzMx
MDEwMDI1NzAzWjAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBAL092tSNLLwniMXpp+SPukdx60Zw2ECIwjr8JQIT
UtGP1NCPpeisVxScS1n19iTmtEdeEcPAneIoRrcJ62WXRjDGGtslyaWZUfseUDjx
eXFb1ZCcOXm6ZM/xCenDrlMbcLlHblWNSYqPxHzUIVeOXRDaQUTYRBU5QPMCCEuH
ii7hAbftJb6itLGjnLXgv1t5EF75cVao020vQQqcWCMR5Fv62PVDGq63yptHFiqY
s8nvgpYy+zTc+XrqS+2q4jgRR6YZysaH4JxaABFvPibJqKUEE89wuZJbgkj1UoeQ
r2of/9zfSnQ4dW59CEKsrcG/tdzcU/5EsRFXUlLgudXaIScCAwEAAaOBkDCBjTAd
BgNVHQ4EFgQUDhhHTcENpq6ZdL7XOoisgI/owh4wUQYDVR0jBEowSIAUDhhHTcEN
pq6ZdL7XOoisgI/owh6hGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENBghQlegAp
pSQJU6dYtMZLv8BPjrZMFTAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjANBgkq
hkiG9w0BAQsFAAOCAQEAk2ntJcU7ihpyUB963kSpNFQ4BrOqehKcUqGhGRDCyJIw
hwKH5knVLlnyMkF+VLq3ohTb52xtIh52xIFjQfuGl10QQwzOjQnT7Nd4VTl1greg
KvSmWeiX926GXG2CxQncbBQglgSf+6bxC2VnnnH20WDVsIWZ6ByR/JMxUPZDn++w
B58nI7ntzSlVkaDnOBqcE6iEhpCWj7jJsSUF20fu4ZoeHGeW4EEM9295phAEBTMz
WI72Ng7YWqjdgPMgauLr66Xr/Te/0rOAfSfkDU8jrMcsWJZgtW9nqFp3p3gf81Qk
BXBpzbPP8B4uG2JBl9z7wcORF7nDrsZFLFuITFXQXg==
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIDVjCCAj6gAwIBAgIQdQ2l1Lfdc2bIk0O7Z8p9sDANBgkqhkiG9w0BAQsFADAW
MRQwEgYDVQQDDAtFYXN5LVJTQSBDQTAeFw0yMzEwMTgwMTU2MzRaFw0zMzEwMTUw
MTU2MzRaMBMxETAPBgNVBAMMCHhpYW9qaW5nMIIBIjANBgkqhkiG9w0BAQEFAAOC
AQ8AMIIBCgKCAQEAq2C34MHi9fdNfeZgI4h4RlLP4qREz4nh64d+3gAI0D6yASRb
HQFySgRyoDXYi2d1HGeIL7tEXVrnJnQ5X0uCBxIC/Ha7axOyVJB89+m/UXP+SIe5
vwsAre5j+9tXEfl81oQLHN+TfFQGfhsPbJZ7MDkzGSpoc0eKBbx4zUBrW7MotwTO
sKmJqjzllxYFWsvSpZKXYlCtWfYlt5UlNqk05dpyTSWzU1HQ9jZ2VI7sME2bXh4C
pQpbGmRWjFnboFDAq0JWyCpBnQLv28fQrFDAfbzd/+pkN+dDV352mG7TFA8cJ0Tq
6Kyx82VWm6G+G5QzQBT/S4XUXDwVS61VeJ3vlQIDAQABo4GiMIGfMAkGA1UdEwQC
MAAwHQYDVR0OBBYEFHc17YNvpmQbx6TW9tPDrkfWy50CMFEGA1UdIwRKMEiAFA4Y
R03BDaaumXS+1zqIrICP6MIeoRqkGDAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQYIU
JXoAKaUkCVOnWLTGS7/AT462TBUwEwYDVR0lBAwwCgYIKwYBBQUHAwIwCwYDVR0P
BAQDAgeAMA0GCSqGSIb3DQEBCwUAA4IBAQCUKqshCVhl3V4DM7gtsZTYqiEU1g6r
0QgNWcPBz4Lrq8Ii4B/iIrueGOPL1I9+GcR3b86kvKGViuo6ahbhV9pgXt4Xhwmm
qGPYyTE4AlXMOhBAKRerrfSmdL1y4fLdYAVLcqMpkYeCuKG48Qg3PAurMATuUZrJ
mSpxreGNhM74NU/MjGO5XTha36IfId2KtUkfczz3ZeQHtpqUuon6w7XYQoGr/aYM
1HB1vLcRhTpt9+FR0GH1GUXv/XzZdRrOqfaIfG1ahvoEfA1rgRieOTXAmpB9932Q
eEvlKED1hqOSI15zondLwPiG2IRllNaj6TIKLWMLmBfd1oPGecgsm9D7
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvwIBADANBgkqhkiG9w0BAQEFAASCBKkwggSlAgEAAoIBAQCrYLfgweL19019
5mAjiHhGUs/ipETPieHrh37eAAjQPrIBJFsdAXJKBHKgNdiLZ3UcZ4gvu0RdWucm
dDlfS4IHEgL8drtrE7JUkHz36b9Rc/5Ih7m/CwCt7mP721cR+XzWhAsc35N8VAZ+
Gw9slnswOTMZKmhzR4oFvHjNQGtbsyi3BM6wqYmqPOWXFgVay9KlkpdiUK1Z9iW3
lSU2qTTl2nJNJbNTUdD2NnZUjuwwTZteHgKlClsaZFaMWdugUMCrQlbIKkGdAu/b
x9CsUMB9vN3/6mQ350NXfnaYbtMUDxwnROrorLHzZVabob4blDNAFP9LhdRcPBVL
rVV4ne+VAgMBAAECggEBAJeDse3G3PajBuLZS4P+wn9B9cMlgiSOfatzJon1M9WQ
qGV0FA3H2phv6DuWf3V4KUTMj83LXby/gn8v4A1NP48qsHMuMbKQPmifOa0g/mFw
EI9lV6X8f0RG8CSaHhepIGKzaPPFAqq3yumw2Oki/ZR77Z5BLQlGZVN+9rpYStJN
VqVDL5MDJZNPwbjutuvw6ifpf3aEEQmoMfP4daGxfZA5rNTG5o5+vrR7yvVdt24X
BTXfbDjnYlJg/XgMT+uoYbAWxeFiH5lthhlb0+imXr5e/7cKbYDgwPCt9WHKStRG
77h/2WNLcUbPLGTarxYPcJQRfLAW6r1RTDytcpofZgECgYEA4lmWG4taiij6MxRO
Pa1LcFSatKHxdWRiAHNUBpx35iQcU6tby4S1XOhUKR4OR65Ti04odmcEEc2UK/v6
FjNUVf0mhbVitzMD4sqXPBP4aETbkVGWfBWCZQNnjMqQo1jyTCvgJ9a1zhwi6HSK
/fAjk+G1Dxqmdke45CDmnXKfvYECgYEAwdOyjVnP9Nm0UDx7xvoMjuboqcBFvGKr
ax1WFgjaPV9CCmcvitTQJp0odAbf80zGMxYqAFX0q2wkUC99qTp1Bo4iyfRuIv9G
xDAhoLZcmQI4+uX2UzXPrm6svvlyaa//RrQx3kS9eMn/i5v6js4ngGBkxL0p6wN9
F6WtPeP9ZBUCgYEAp/T985ZmKprZfUmV/SI4FjRRT7PTLd688cSiFv3H4lftRRCk
XtIsmbIzsQcCZaIvj/EBCUrLtEItrq2dFxgjfmMIULMVewc53PGjYwsWiph9rMkz
twNm7HmoPsqYpPz9XhQ4kpc59KTgKklAUcn9PGCBL6IA30e9JFpdhXtmmQECgYB1
lofZJyZ5ReYVU0xIX4Rk4YM/EI1+B2I1XpvOTFqSJws6onT+RbNt6aQUF+Ofh/Eq
JwUeJQeFQ9sX5mfW1ccPTgWe/bIfez0kYorUJC4zCV0mIYL54kh3a19TkKOvqH03
GLS0QoGsGOf2e49bOYhPYqtfi981W211fiaGyJz+LQKBgQDPBHapHKdceSmDP2JJ
SzH6B5PGHAblkfM5j1FQ4m76LXrHTHHjNf7FYWpdA0I0CJ7aMQHYPA5SDTEhSdYf
GZWkcqcGzSKBTL4XYOTki2+UAaR6yaeF4Nhhxmzhh260t2IqcG5cFz1LoDN25vc9
wisr5ovExFiJTcgV+aqpkf3hvQ==
-----END PRIVATE KEY-----
</key>
remote-cert-tls server
cipher AES-256-CBC
verb 3账号的管理(增删改查)
新增账号一键脚本
#!/bin/bash
read -p "请输入用户的姓名拼音(如:${NAME}): " NAME
cd /opt/easy-rsa/
./easyrsa gen-req ${NAME} nopass <<EOF
EOF
./easyrsa sign client ${NAME} <<EOF
yes
EOF
if [ ! -d "/etc/openvpn/client/${NAME}" ]; then
mkdir "/etc/openvpn/client/${NAME}"
else
echo "目录已存在,可能已经存在相关文件。"
fi
cp pki/private/${NAME}.key /etc/openvpn/client/${NAME}/
cp pki/issued/${NAME}.crt /etc/openvpn/client/${NAME}/
cp pki/ca.crt /etc/openvpn/client/${NAME}/
cd /etc/openvpn/client/${NAME}/
cp /etc/openvpn/client/zhangjiaao/client.ovpn ./
# 检查 client.ovpn 文件是否存在
if [ ! -f "client.ovpn" ]; then
echo "错误: client.ovpn 文件不存在。请确保脚本和 client.ovpn 文件在同一目录下。"
exit 1
fi
# 替换 cert 行
sed -i "s/^cert .*/cert ${NAME}.crt/" client.ovpn
# 替换 key 行
sed -i "s/^key .*/key ${NAME}.key/" client.ovpn
echo "替换完成。请检查 client.ovpn 文件,确保文件名已被正确替换。"
tar -czvf ./${NAME}.tar.gz ./*使用过程
root@yaosoft:/opt/easy-rsa# bash start.sh
请输入用户的姓名拼音(如:): ceshi
..............................
cd /etc/openvpn/client/ceshi/
ls
ca.crt ceshi.crt ceshi.key ceshi.tar.gz client.ovpn
#把gz压缩包发送给用户并且加上用户手册即可
